In today’s digital landscape, the increasing reliance on data-driven solutions has underscored the necessity of rigorous data privacy principles in software development. As consumers become more aware of their rights and the implications of data misuse, businesses are tasked with not only safeguarding sensitive information but also building trust with their users. This article explores the critical framework of data privacy principles and their integration into the software development lifecycle. By adopting a proactive approach to data privacy, organizations can enhance compliance with regulatory requirements, mitigate risks, and foster a culture of accountability. We will delve into best practices, key considerations, and actionable strategies that developers and project managers can implement to ensure that data privacy is not merely an afterthought but a foundational component of their software solutions. Embracing these principles not only aligns with ethical standards but also positions businesses as leaders in a marketplace that increasingly prioritizes data security and user trust.
Table of Contents
- Understanding Data Privacy Principles and Their Importance in Software Development
- Integrating Privacy by Design Methodologies into the Development Lifecycle
- Conducting Comprehensive Data Risk Assessments to Enhance Privacy Protections
- Ensuring Compliance with Regulatory Standards through Effective Documentation and Training
- To Wrap It Up
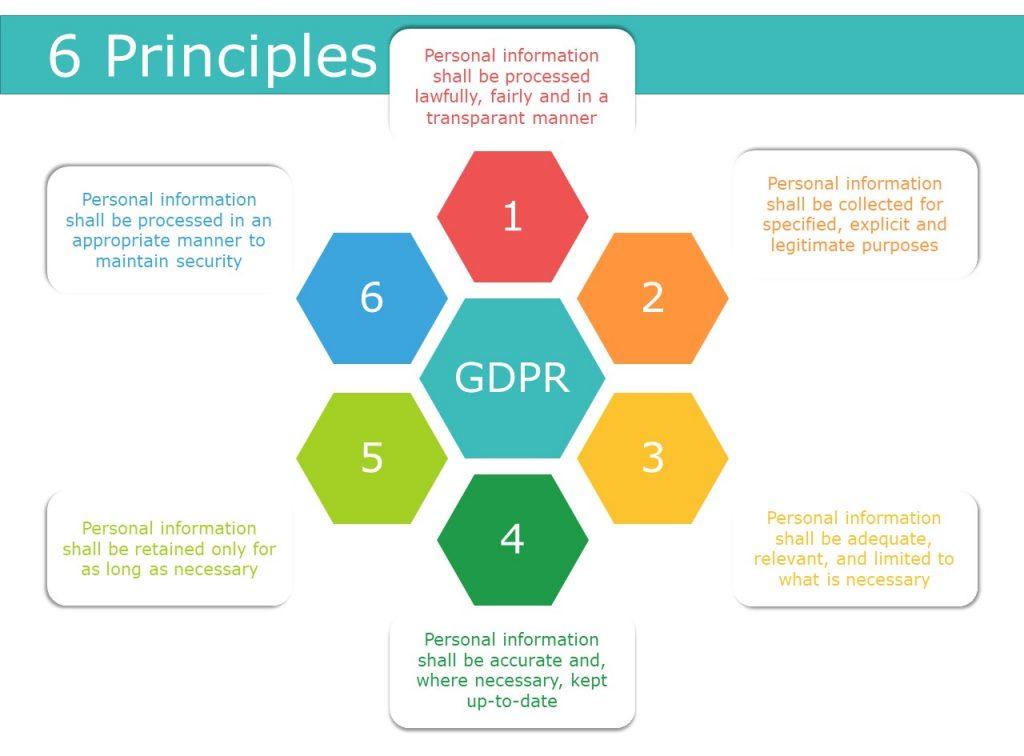
Understanding Data Privacy Principles and Their Importance in Software Development
In the realm of software development, adhering to robust data privacy principles is essential for building trust and safeguarding user information. Implementing these principles ensures compliance with regulations like GDPR and CCPA, which ultimately protects both the developers and users alike. Key elements that constitute fundamental data privacy principles include:
- Data Minimization: Collect only the data necessary for specific purposes.
- Transparency: Clearly inform users about data collection methods and usage.
- Accountability: Establish mechanisms for data stewardship and compliance monitoring.
- Security: Implement robust encryption and data protection measures to secure user data.
Integrating these principles into the software development lifecycle not only fulfills legal obligations but also enhances user confidence and satisfaction. Moreover, companies that prioritize data privacy can experience a significant competitive advantage by differentiating their products in a crowded market. To illustrate these principles effectively, the table below highlights the correlation between key data privacy principles and their implications in software features:
| Data Privacy Principle | Software Feature Implication |
|---|---|
| Data Minimization | User-controlled data sharing settings |
| Transparency | Clear user agreements and privacy notices |
| Accountability | Regular audits and compliance reports |
| Security | Robust authentication and access controls |
Integrating Privacy by Design Methodologies into the Development Lifecycle
To achieve effective integration of privacy by design methodologies, organizations must embed privacy considerations into every phase of the software development lifecycle. This approach begins at the requirements gathering stage, where stakeholders should clearly define data protection goals alongside functional requirements. Engaging a cross-functional team, including legal and compliance experts, ensures that privacy regulations and best practices are addressed from the outset. Key strategies for integration include:
- Conducting Privacy Impact Assessments (PIAs) to identify potential risks and mitigation strategies.
- Establishing clear data governance frameworks that dictate how data is collected, stored, and processed.
- Utilizing pseudonymization and encryption techniques to minimize data exposure.
As development progresses, continuous monitoring and testing for compliance with privacy standards should be instilled within the agile methodology. This ongoing vigilance fosters a culture of accountability and responsiveness to emerging privacy challenges. Additionally, teams should adopt practices such as:
- Programming with Secure by Design principles to limit vulnerabilities.
- Implementing incident response plans that specifically address data breaches and unauthorized access.
- Conducting regular training for developers and other stakeholders to raise awareness of privacy issues.
| Phase of Development | Action Items |
|---|---|
| Planning | Privacy assessments, stakeholder engagement |
| Design | Architecture reviews, threat modeling |
| Implementation | Secure coding practices, regular audits |
| Testing | Privacy testing, code reviews |
Conducting Comprehensive Data Risk Assessments to Enhance Privacy Protections
In an era where data breaches are prevalent and privacy concerns are paramount, conducting in-depth assessments of data-related risks is crucial for organizations striving to safeguard personal information. By systematically identifying potential vulnerabilities associated with data handling, businesses can implement tailored strategies that address specific threats and bolster their privacy frameworks. Key elements of this risk assessment process should include:
- Identifying Sensitive Data: Determine what data is stored, processed, and shared.
- Assessing Potential Risks: Analyze the likelihood and impact of data breaches.
- Evaluating Existing Controls: Review current measures and their effectiveness against identified risks.
- Creating Mitigation Plans: Develop strategies for minimizing risks based on assessment findings.
To effectively enhance privacy protections, organizations should prioritize ongoing education and training for employees about data handling practices. Regular workshops and updates can ensure that staff remains vigilant and informed about the latest privacy regulations and technologies. Moreover, utilizing a structured framework for monitoring compliance can significantly improve accountability in data management processes. This framework could include:
| Framework Component | Description |
|---|---|
| Data Governance | Establishing policies for data collection, usage, and sharing. |
| Compliance Audits | Regular assessments to ensure adherence to privacy laws and standards. |
| Incident Response | Protocols for addressing data breaches effectively. |
Ensuring Compliance with Regulatory Standards through Effective Documentation and Training
To navigate the complexities of adhering to regulatory standards, organizations must prioritize robust documentation processes. Effective documentation serves as both a roadmap and a safeguard, ensuring that every stakeholder understands their responsibilities relating to data privacy. Key documentation practices include:
- Clear data usage policies
- Detailed records of data processing activities
- Regular updates reflecting changes in legislation
- Comprehensive training manuals for employees
These practices not only foster transparency but also enhance accountability, minimizing the risk of non-compliance and potential penalties.
In addition to documentation, ongoing training plays a critical role in maintaining compliance with data privacy standards. Training sessions should be designed to raise awareness about regulatory requirements and instill effective data handling practices among employees. A well-structured training program might include:
| Training Component | Description |
|---|---|
| Introductory Sessions | Overview of data privacy regulations |
| Hands-On Workshops | Practical scenarios and role-playing |
| Regular Refreshers | Updated information on new laws and best practices |
By implementing these components, companies can ensure that their teams remain compliant and vigilant in the protection of sensitive data.
To Wrap It Up
the integration of data privacy principles into software development is not merely a regulatory obligation; it is an ethical imperative that fosters trust and secures competitive advantage in an increasingly data-driven marketplace. By prioritizing privacy from the outset—adopting strategies such as data minimization, employing robust encryption methods, and conducting regular privacy audits—organizations can mitigate risks while enhancing user confidence in their products. As privacy regulations continue to evolve, it is essential for companies to remain proactive, embed a culture of privacy within their teams, and stay informed about industry best practices. Ultimately, a commitment to data privacy not only protects consumers but also reinforces a company’s reputation as a responsible and forward-thinking leader in the tech landscape. As we move forward, let us embrace these principles as integral to the software development process, ensuring that the protection of personal data remains at the forefront of our innovation strategies.