Title:
In today’s digitally driven landscape, where data has become the lifeblood of innovation and strategic decision-making, the importance of integrating data privacy into software development practices cannot be overstated. As businesses strive to harness the power of information, they also face mounting regulatory pressures and heightened consumer expectations regarding the protection of personal data. The challenge for software developers and organizations alike is twofold: to create robust, innovative solutions while safeguarding sensitive information from breaches and unauthorized access.
This article explores the critical intersection of data privacy and software development, outlining best practices and strategies for embedding privacy considerations throughout the software lifecycle. By prioritizing data protection from the initial design phase through to deployment and beyond, organizations can not only comply with regulations such as the GDPR and CCPA but also build trust with customers, ultimately creating a competitive advantage in a conscientious market. As we navigate the complexities of this essential integration, we will address the emerging technologies and frameworks that facilitate compliance without compromising functionality, ensuring that privacy is an integral component of effective software development.
Table of Contents
- Understanding the Importance of Data Privacy in Software Development
- Best Practices for Incorporating Data Privacy from Concept to Deployment
- Establishing a Culture of Data Privacy within Development Teams
- Monitoring and Compliance: Ensuring Ongoing Data Privacy Safeguards
- To Conclude
Understanding the Importance of Data Privacy in Software Development
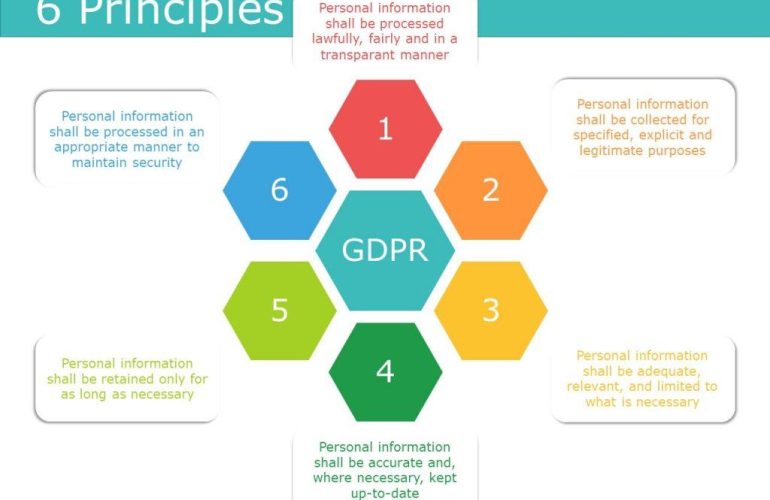
In an era where data breaches and privacy concerns dominate headlines, the integration of data privacy in software development has become paramount. As developers create applications that often handle sensitive information, understanding the implications of data privacy ensures not only regulatory compliance but also fosters trust between users and organizations. It necessitates an awareness of data protection regulations, such as the GDPR and CCPA, which can impose significant penalties for non-compliance. Therefore, embracing a privacy-first mindset from the initial stages of development can prevent potential legal issues and enhance the overall security posture of the software.
Establishing a robust framework for data privacy involves several key practices that must be woven into the development lifecycle. These include:
- Data Minimization: Collect only the data necessary for the intended purpose.
- Anonymization Techniques: Ensure personal identification information is protected.
- Access Controls: Limit data access based on roles within the organization.
- Regular Audits: Conduct periodic assessments to identify potential vulnerabilities.
- Security Training: Equip development teams with knowledge about data privacy best practices.
| Data Privacy Strategies | Benefits |
|---|---|
| Incorporating Privacy by Design | Enhances user trust and aligns with regulations |
| Regular Compliance Checks | Reduces legal risks and potential fines |
| Transparency in Data Usage | Improves user engagement and satisfaction |
Best Practices for Incorporating Data Privacy from Concept to Deployment
To ensure data privacy is a foundational element of software development, it is crucial to adopt a privacy-by-design approach from the initial stages of a project. This involves integrating privacy considerations into every phase of the software development lifecycle, from planning and design to testing and deployment. Key activities include:
- Conducting thorough privacy impact assessments to identify and mitigate potential risks early in the process.
- Engaging stakeholders in discussions about data privacy requirements to ensure alignment and transparency.
- Implementing secure coding practices and regular training for developers to stay updated on the latest privacy regulations and security threats.
Moreover, leveraging tools and frameworks that facilitate compliance will not only streamline development but also enhance trust with users. Consider employing automated testing for privacy features to catch security vulnerabilities promptly. Additionally, it is essential to maintain an open line of communication regarding data handling practices with end-users. A clear presentation of how their data will be collected, used, and protected can be achieved through:
| Component | Description |
|---|---|
| Privacy Notices | Clear and concise information regarding data collection and usage. |
| User Consent Mechanisms | Tools for obtaining explicit consent from users before data collection. |
| Data Access Requests | Processes for users to easily request access to their personal data. |
Establishing a Culture of Data Privacy within Development Teams
Fostering a strong commitment to data privacy among development teams is essential for creating software that not only meets business goals but also safeguards user information. To achieve this, organizations should invest in comprehensive training programs that emphasize data protection principles and regulatory compliance. These training sessions can cover crucial topics, such as:
- Understanding data privacy laws: Familiarize team members with regulations like GDPR and CCPA.
- Implementing secure coding practices: Teach developers how to write code that minimizes vulnerabilities.
- Data minimization principles: Encourage the team to collect only what is necessary for the functionality of the application.
Furthermore, embedding data privacy into the development lifecycle can significantly bolster a company’s reputation and customer trust. This integration can be achieved by establishing clear data governance policies that outline roles and responsibilities across teams. A collaborative approach should incorporate regular privacy impact assessments at key milestones and foster open communication channels between development, legal, and compliance teams to address concerns promptly. Consider implementing tools that facilitate this collaboration, such as:
| Tool | Purpose |
|---|---|
| Jira | Track data privacy tasks and issues |
| Confluence | Document data privacy policies and best practices |
| Slack | Facilitate real-time communication on privacy concerns |
Monitoring and Compliance: Ensuring Ongoing Data Privacy Safeguards
To effectively safeguard data privacy within software development processes, continuous monitoring and compliance checks are essential components. Organizations must establish a robust framework that allows for regular audits and assessments of data usage across applications. This framework should include:
- Automated Compliance Tools: Utilizing software that monitors data activity in real-time, ensuring adherence to privacy regulations.
- Data Access Controls: Implementing strict access protocols to limit exposure to sensitive information.
- Regular Training Programs: Ensuring that all team members are aware of the latest data privacy laws and best practices.
Furthermore, developing a feedback loop from the compliance checks can foster a culture of accountability and adaptation. This involves regular reporting on privacy metrics to stakeholders, which could include:
| Metric | Description | Frequency |
|---|---|---|
| Data Breach Incidents | Number of breaches reported | Monthly |
| User Access Reviews | Assessing access rights to sensitive data | Quarterly |
| Compliance Training Completion | % of staff completed required training | Bi-Annually |
By leveraging these tactics, software development teams can not only comply with regulations but also instill confidence among users regarding their data security protocols.
To Conclude
the integration of data privacy into effective software development is not merely an optional enhancement but a critical component of a responsible and sustainable development strategy. As we navigate an increasingly data-driven landscape, organizations must prioritize robust privacy measures that align with regulatory requirements and resonate with the expectations of their end-users.
By embedding privacy considerations throughout the software development lifecycle, from initial design to deployment and beyond, businesses can not only safeguard sensitive information but also build trust with their customers. Investing in privacy-centric development practices not only mitigates risk but also enhances brand reputation and fosters customer loyalty in a competitive market.
Ultimately, the commitment to data privacy is not just a legal obligation; it is a strategic advantage that can differentiate organizations in their pursuit of excellence. As we move forward, let us embrace the opportunity to lead with integrity, ensuring that every line of code reflects our dedication to protecting the privacy of individuals and the integrity of data.